Note:I translated Japanese into English using Google Translate.
Thank you, Google.
Change the ACL of the object on AD and check ADTimline. Use AD ACL Scanner as a tool to check the ACL of AD objects.
AD Timeline-FIRST TC Page 22 has an entry for "AD replication metadata vs security event logs". Check the ACL and compare the security log.
Allow the Alice account the rights needed by DCsync. Below, I set up two permissions related to replication.
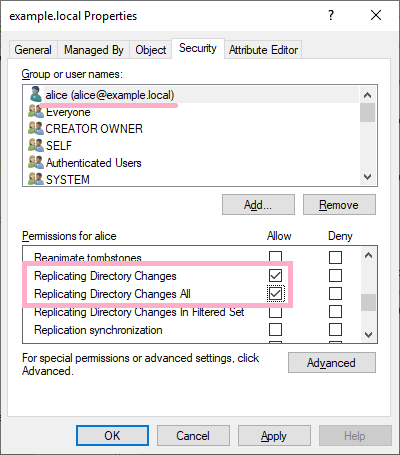
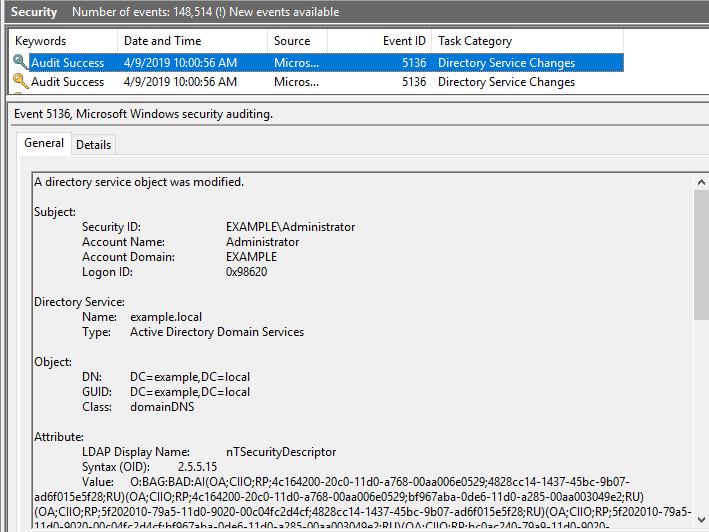
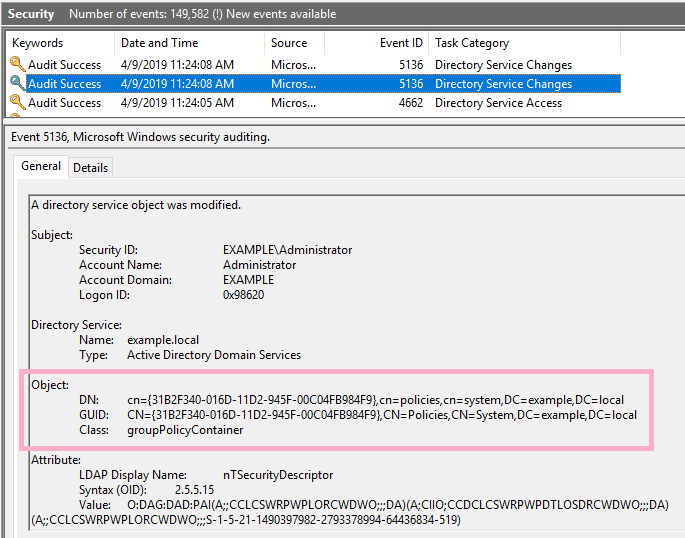
Two event ID 5136 were recorded in the security log.
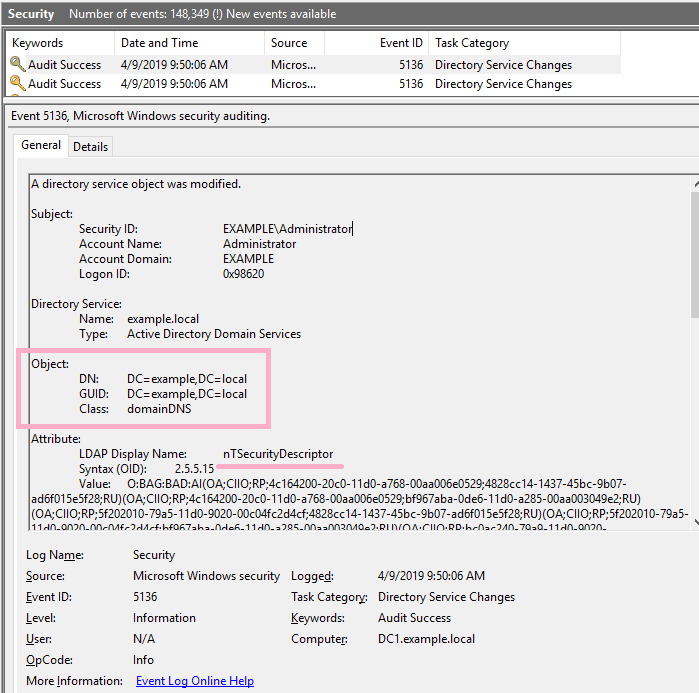
Run AD ACL Scanner and check the report. I can view the privileges of Alice account.
Two entries, Critical and Warning, are displayed.
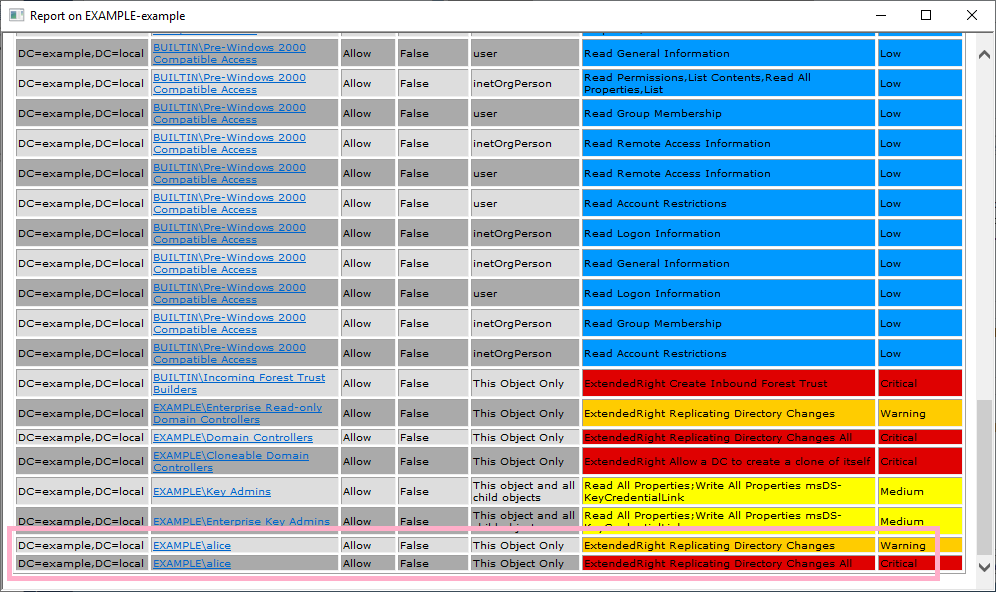
Execute ADTimeline and check "nTSecurityDescriptor". The time is slightly different from security log ID 5136.
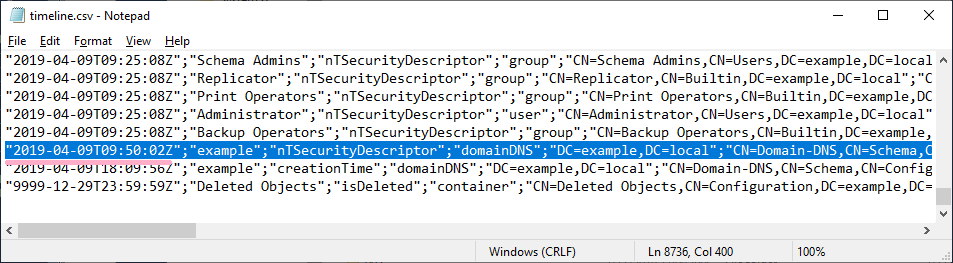
Remove the access rights of Alice account and view the timeline in ADTimeline.
On the timeline, the time stamp where I added Alice disappears, and a record of the time stamp where Alice was deleted is displayed.
Interesting :-)
Next, let's change the GPO ACL. Add an Alice account to Delegation.
Default Domain Policy: {31B2F340-016D-11D2-945F-00C04FB984F9}
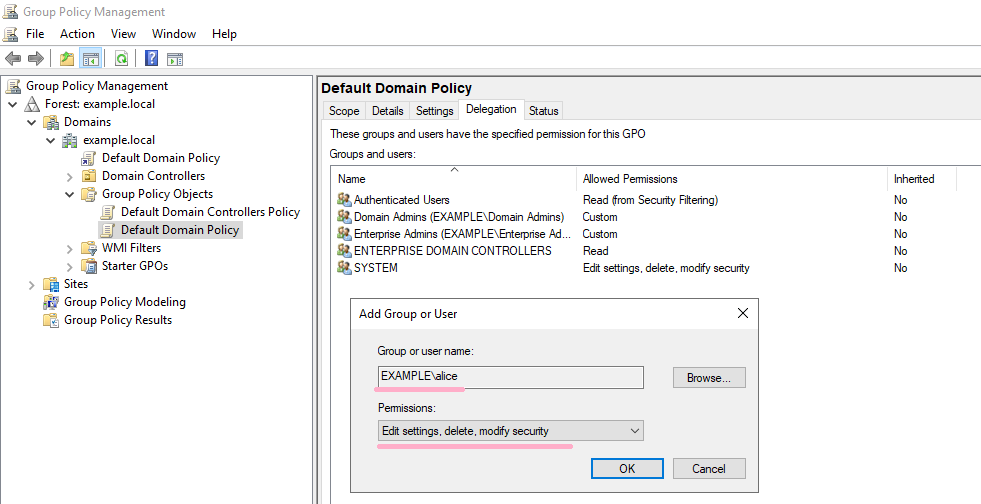
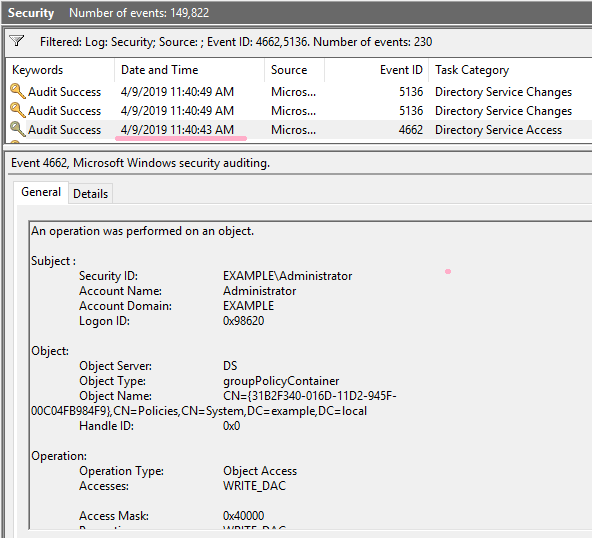
Event ID 4662 is recorded in the security log. Two more ID 5136 records are recorded.
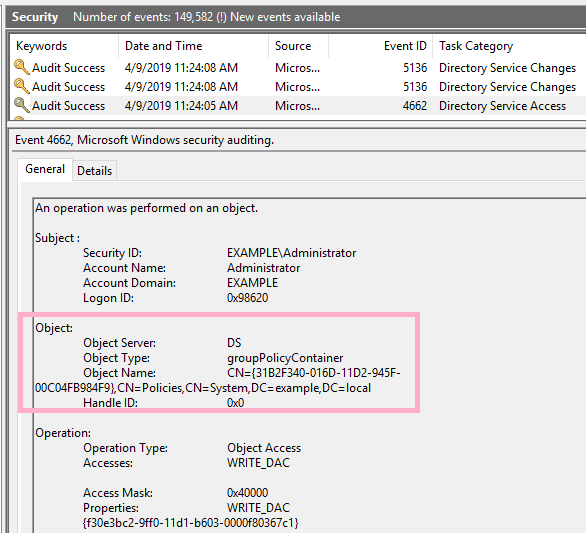
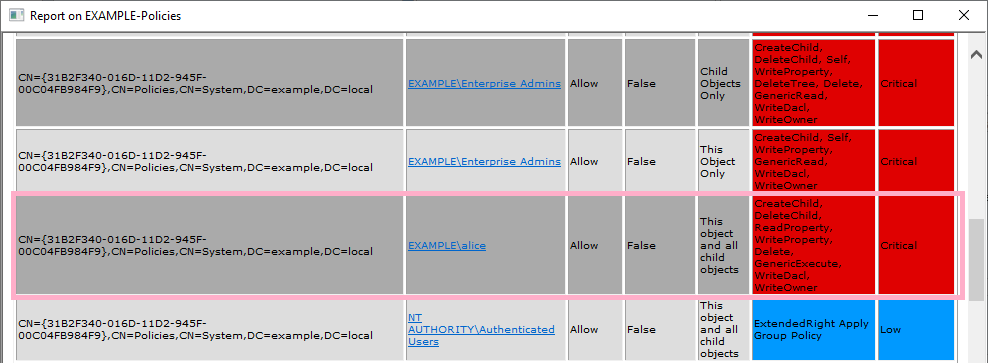
Check the ACL of Default Domain Policy {31B2F340-016D-11D2-945F-00C04FB984F9}. I can discover the privileges of Alice account.
Check the timeline. The timestamp is the same as event ID 4662.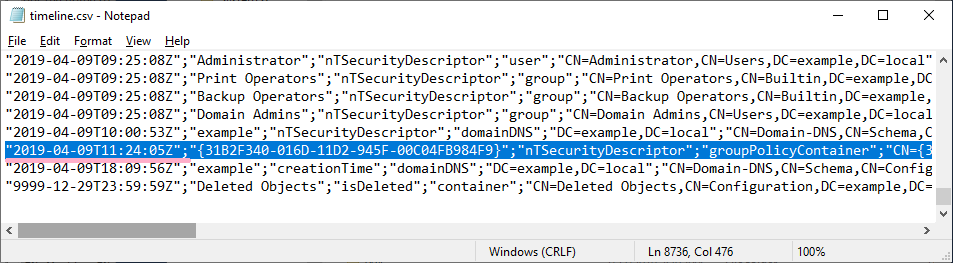
Remove the access rights of Alice account that I added earlier from the GPO.
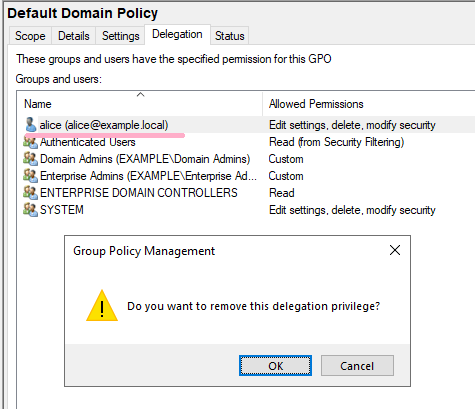
In the security log, ID 4662 and ID 5136 are recorded.
Create a timeline and compare it with the timestamps in the security log.
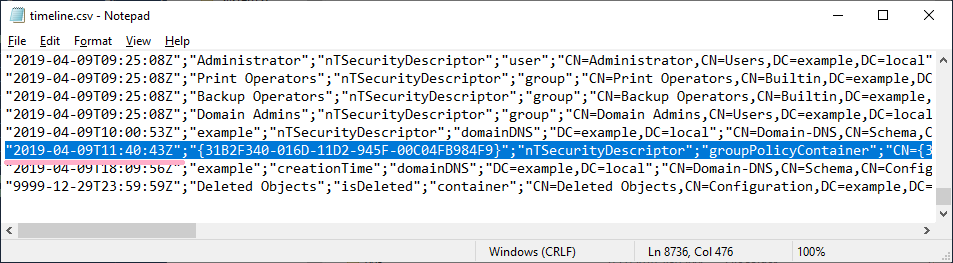
Next, allow AdminSDHolder full control of Bob's account. (This change is the result of a previous test with DCshadow.)
This setting allows access by Bob account to Domain Admins group etc.
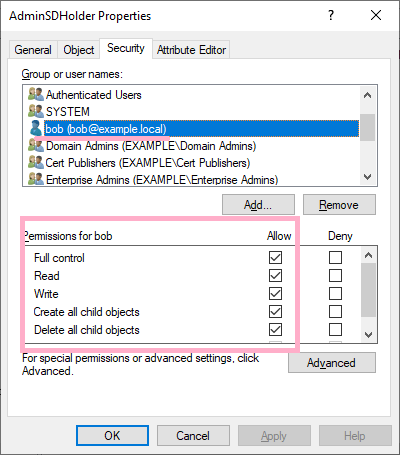
Let's check the ACL. The report shows that Bob's account has full control.
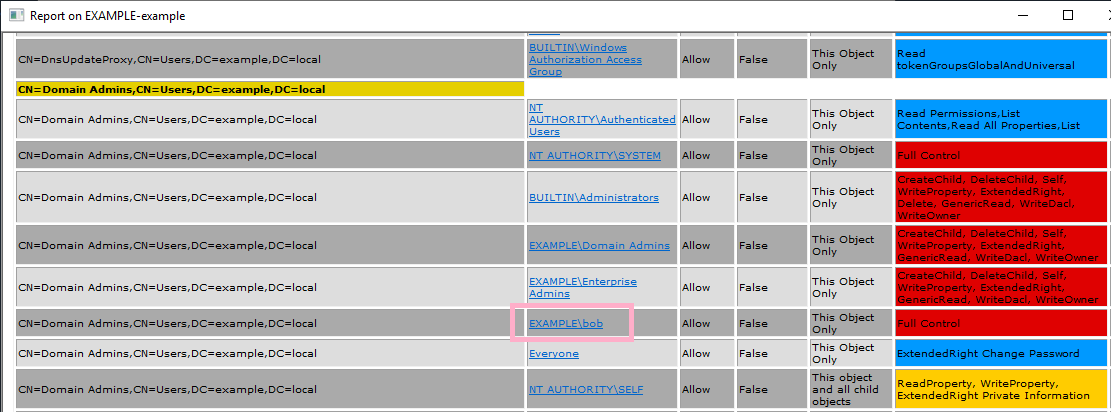
Execute ADTimeline and search AdminSDHolder to find out the following events.
ftimeLastOriginatingChange : 2019-04-08T11:28:47Z
Name : AdminSDHolder
pszAttributeName : nTSecurityDescriptor
ObjectClass : container
DN : CN=AdminSDHolder,CN=System,DC=example,DC=local
ObjectCategory : CN=Container,CN=Schema,CN=Configuration,DC=example,DC=local
SamAccountName :
dwVersion : 4
WhenCreated : 2019-01-20 19:19:55Z
Member :
ftimeCreated :
ftimeDeleted :
SID :
pszLastOriginatingDsaDN : CN=NTDS Settings,CN=DC1,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configur
ation,DC=example,DC=local
uuidLastOriginatingDsaInvocationID : c9e22352-ca47-436a-aeb2-38228298896d
usnOriginatingChange : 114772
usnLocalChange : 114772
Next,
Change the security of Bob account. Change Owner to Bob and set Deny to Everyone.
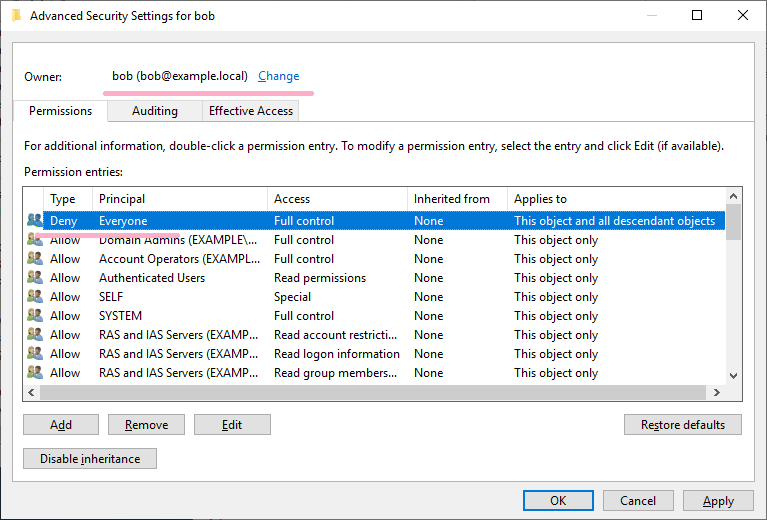
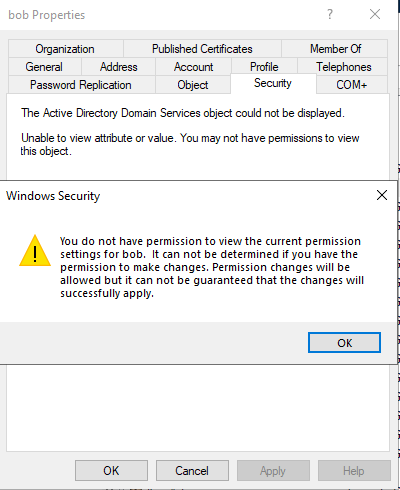
If try to view Bob's account security information, it will be denied.
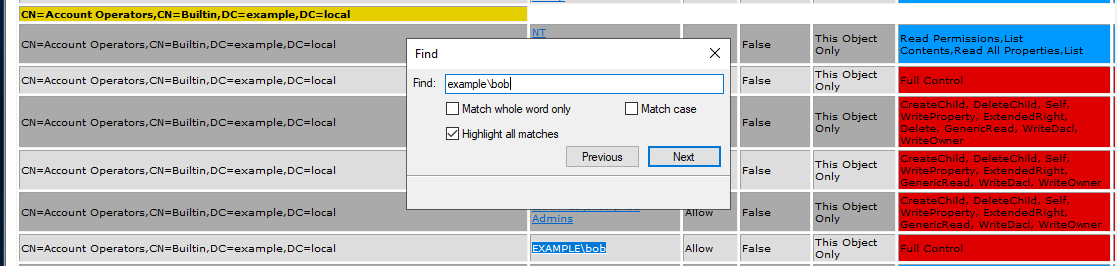
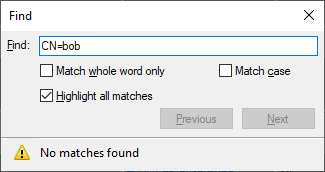
Scan the ACL again and view the report. I can see the permissions granted to Bob account, but the report does not include information about the Bob account itself.
Reference URL:
An ACE Up the Sleeve:Designing Active Directory DACL Backdoors
https://specterops.io/assets/resources/an_ace_up_the_sleeve.pdf
