Windows Defender Remote Credential Guard and RestrictedAdmin mode.
Note:I translated Japanese into English using Google Translate.
Thank you, Google.
Windows Defender Remote Credential Guard is available for Windows 10 and Windows Server 2016.
Is there any way to check if Remote Credential Guard was used with RDP connection?
I checked some event logs but could not identify the use of /remoteGuard.
Remote Credential Guard needs to enable RestrictedAdmin mode. I'm concerned about enabling RestrictedAdmin mode. ->
「Passing the hash with native RDP client (mstsc.exe) - Blog | Michael Eder」
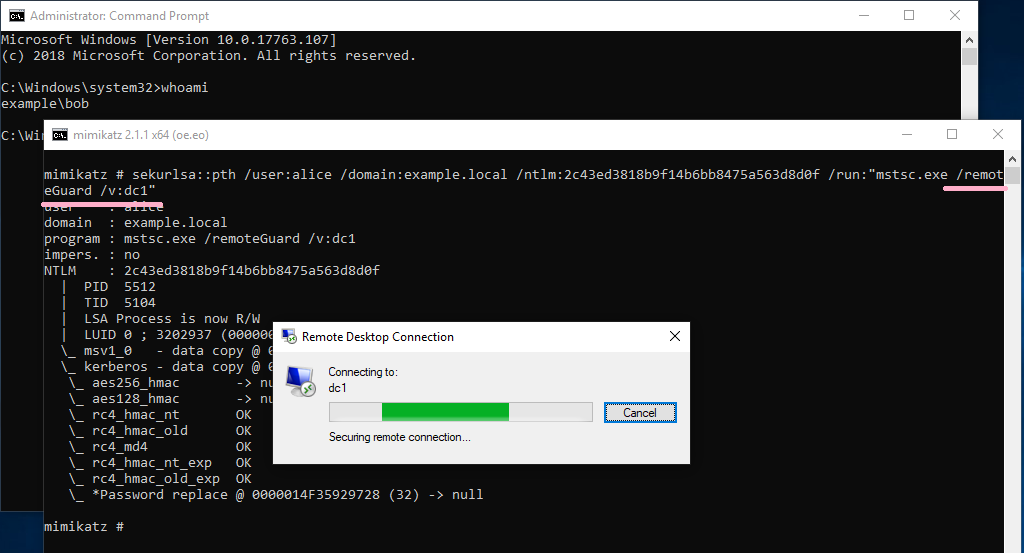
So I continue to look for information to identify.
---
I enabled RDP on Windows Server 2016 and NLA option is checked. The domain user Alice has been added to Remote Desktop Users.
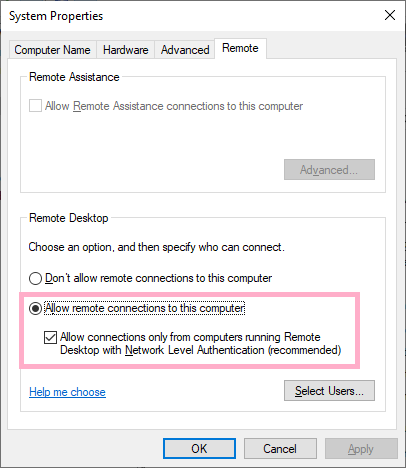
Set the DisableRestrictedAdmin value in the registry and enable RestrictedAdmin mode.

Execute mstsc.exe on Windows 10(PC1) with /remoteGuard option. This verification did not set up a group policy.
mstsc.exe /remoteGuard
If I enter a computer name, the user's item will be grayed out automatically.
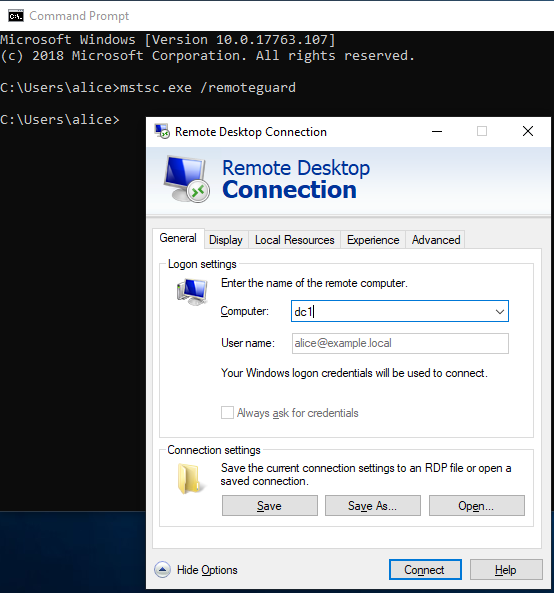
Connect to computer DC1 and view the event log.
DC1
Check the event log records. The following is event logs of DC1 which received RDP connection.
(1) ID 1149 does not record user names, but ID 21 and 22 record Alice.
2019-05-01T10:38:29.350975900Z Microsoft-Windows-TerminalServices-RemoteConnectionManager
ID 1149
Remote Desktop Services: User authentication succeeded:
User:
Domain:
Source Network Address: 192.168.100.10
2019-05-01T10:38:32.690529600Z Microsoft-Windows-TerminalServices-LocalSessionManager
ID 21
Remote Desktop Services: Session logon succeeded:
User: EXAMPLE\alice
Session ID: 2
Source Network Address: 192.168.100.10
ID 22
Remote Desktop Services: Shell start notification received:
User: EXAMPLE\alice
Session ID: 2
Source Network Address: 192.168.100.10
(2) Let's check the security log.
Check NLA event ID 4624 Logon type 3. The item of "Restricted Admin Mode:" is displayed as "-".

(3) Event ID 4648

(4) Event ID 4624 Logon Type 10, "Restricted Admin mode" is displayed as "NO".

I could not determine from the event log whether /remoteGuard was used.
Next, check the log when logged on in RestrictedAdmin mode.

It can be confirmed by the record of ID 4624 logon Type 10, "Restricted Admin mode" is displayed as "Yes".

PC1
If /remoteGuard or /restrictedAdmin is specified as an option of mstsc.exe, ID 4648 is not recorded in the security log.
Verification environment: Windows Server 2019 1809, Windows 10 1809, Time zone UTC
Reference URL:
#mimikatz can pass-the-ticket (Kerberos) for RDP with "restrictedadmin" support - protected users, you're welcome! pic.twitter.com/PBoUAjvki3
— 🥝 Benjamin Delpy (@gentilkiwi) March 1, 2014
