Note:I translated Japanese into English using Google Translate.
Thank you, Google.
There is a great article called “Windows Server Data Dedupliction and Forensic Analysis”.
If you are interested in the Dedupliction feature, I recommend that you read it first.
---
I used Windows Server 2019 and enabled the Data Deduplication function on volume F :.
Day 0 is set so that deduplication is performed immediately.
Two folders were created and several JPEG files were placed in each folder. I copied the same JPEG file, so these files should be deduplicated.


Check the deduplication status. None of the files have been deduplicated yet.

Use the Start-DedupJob command to execute deduplication.
Start-DedupJob -Type Optimization -Volume F: -Memory 100 -Cores 100 -Priority High

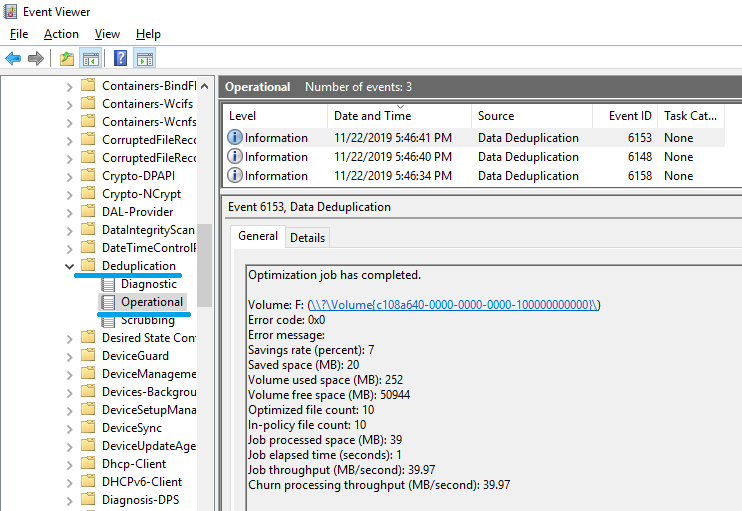
Ten files have been deduplicated.

Use Windows Explorer to display the file properties. You can see that the size on the disk is zero.

The file attribute is "AL". “L” means Reparse Point. By looking at the “size on disk” or “attribute” in Windows Explorer, I can find a deduplicated file.

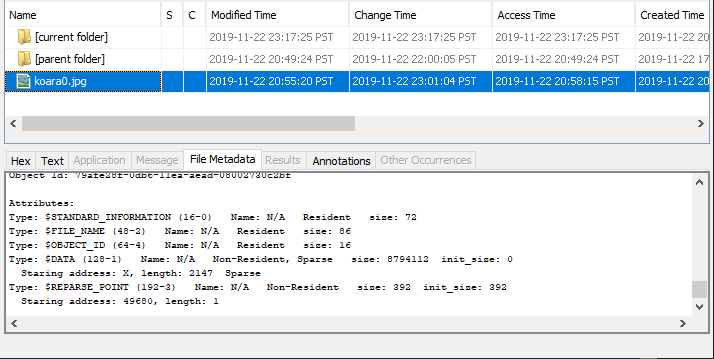
Let's check the attributes of the FILE record using Autopsy 4.13.0.

The staring address of $DATA attribute is “X” and "Sparse". The length is 980.
Check the FILE record of the JPEG file using FTK Imager. The value of DataRun is “02E003”. 0x03E0 ⇒ 992
Why doesn't the length match the Autopsy result?

Check "$REPARSE_POINT (0xC0)". This attribute is Non-Resident, and the attribute data is stored in cluster number 49662.

Refer to cluster number 49662. The first 4 bytes are “Reparse Type” and the value of “IO_REPARSE_TAG_DEDUP” is “0x80000013”.

Unfortunately, I couldn't find any information about the structure of IO_REPARSE_TAG_DEDUP.
Let's check the USN Journal using another file.
I prepared two images and deduplicated them.

Parse $J. And I discover that I misspelled "Koala" :-)

Finally, delete one of the deduplicated files.

Check the attributes in the FILE record of the deleted file.

Try to deduplicate the “Koala” image again.


There was no change in the deduplication status of "Koala".
Verification environment: Windows Server 2019 1809.
Reference URL:
