Note:I translated Japanese into English using Google Translate.
Thank you, Google.
Summary:
- I added the Bob account to the "Domain Admins" group and deleted it from the group. You can check this operation with ADTimeline.
- Run DCsync with Alice account. This operation could not be confirmed on the timeline.
- Using DCshadw, set the SIDHsitory of the Bob account. The operation by DCshadow can be confirmed with ADtimeline.
----------
[Note]Please be aware that the verification method not be sufficient.
I checked the ADTimeline about Bob account last week.(Last week, I was not reading "README.md" carefully.)
Bob account is a regular user, today's test I would like to set Bob high privilege. Add the Bob account to the Domain Admins group and then delete it from the group.
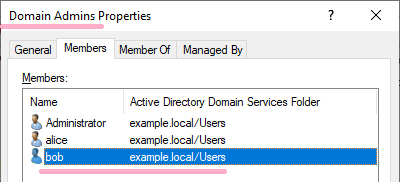
DC1: 2/23/2019 1:29:15 AM EID 4728 A member was added to a security-enabled global group.(Bob)
DC2: 2/23/2019 1:35:23 AM Log on to PC1 with Bob account
DC2: 2/23/2019 1:40:50 AM Bob account log off.
Since Bob was a Domain Admins group, it appears on the timeline. I can check the following records on ADtimeline.(I have not set up a custom group.)
ftimeLastOriginatingChange : 2019-02-23T01:35:22Z
Name : bob
pszAttributeName : lastLogonTimestamp
ObjectClass : user
DN : CN=bob,CN=Users,DC=example,DC=local
ObjectCategory : CN=Person,CN=Schema,CN=Configuration,DC=example,DC=local
SamAccountName : bob
dwVersion : 2
WhenCreated : 2019-02-11 07:06:37Z
Member :
ftimeCreated :
ftimeDeleted :
SID : S-1-5-21-1490397982-2793378994-64436834-1601
pszLastOriginatingDsaDN : CN=NTDS Settings,CN=DC2,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configur
ation,DC=example,DC=local
uuidLastOriginatingDsaInvocationID : 97c9ab0f-143e-4218-96fb-a6bdc442af7e
usnOriginatingChange : 24760
usnLocalChange : 45216
Delete the Bob account from the Domain Admins group.
DC1: 2/23/2019 1:44:06 AM EID 4729 A member was removed from a security-enabled global group.(Bob)
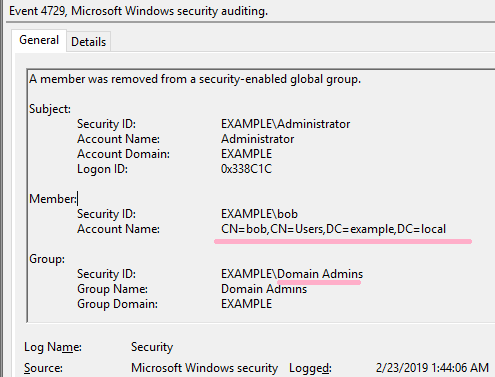
On ADTimeline, I can check the date and time Bob was added and deleted to Domain Adminsin the following record.
ftimeLastOriginatingChange : 2019-02-23T01:44:06Z
Name : Domain Admins
pszAttributeName : member
ObjectClass : group
DN : CN=Domain Admins,CN=Users,DC=example,DC=local
ObjectCategory : CN=Group,CN=Schema,CN=Configuration,DC=example,DC=local
SamAccountName : Domain Admins
dwVersion : 2
WhenCreated : 2019-01-20 19:20:35Z
Member : CN=bob,CN=Users,DC=example,DC=local
ftimeCreated : 2019-02-23T01:29:15Z
ftimeDeleted : 2019-02-23T01:44:06Z
SID : S-1-5-21-1490397982-2793378994-64436834-512
pszLastOriginatingDsaDN : CN=NTDS Settings,CN=DC1,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configur
ation,DC=example,DC=local
uuidLastOriginatingDsaInvocationID : c9e22352-ca47-436a-aeb2-38228298896d
usnOriginatingChange : 45230
usnLocalChange : 45230
Next test, I would like to grant high privilege by using Bob's SIDHistory.
Log on to PC1 with Alice account.Run Mimikatz on Alice account and check administrator's information using DCsync.
DC2: 2/23/2019 1:53:36 AM EID 4662 An operation was performed on an object.
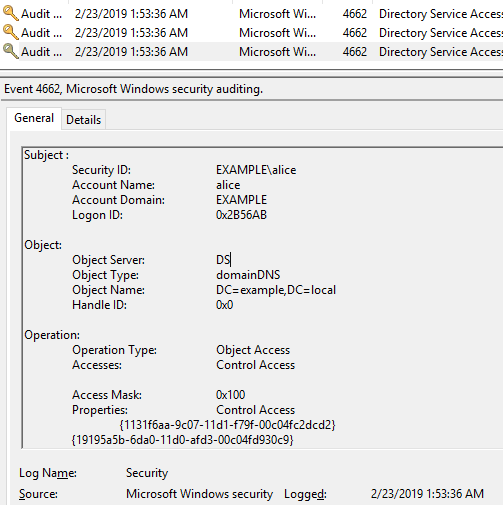
On ADtimeline, I can confirm Alice 's logon, but I could not find a record related to DCSync. (I guess that metadata replication does not occur.)
Run DCshadow with the Alice account and set the Administrator's SID in the sidHistory of the Bob account.
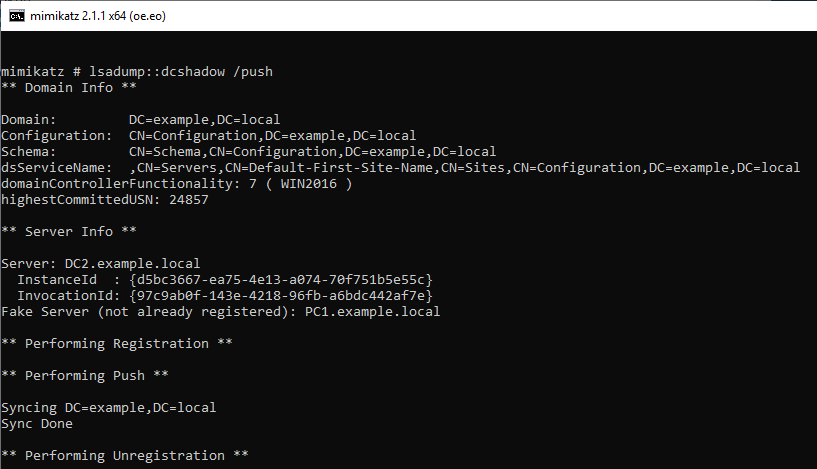
DC2: 2/23/2019 2:12:15 AM EID 4662 An operation was performed on an object.
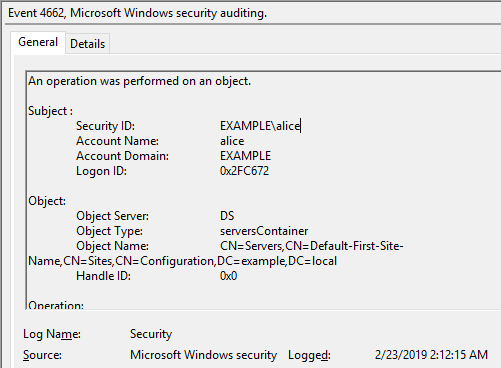
On the ADTimeline, I can confirm this operation with several records. "PC1" that operated DCshadow is displayed.
ftimeLastOriginatingChange : 2019-02-23T02:12:15Z
Name : PC1
DEL:de838231-3f87-47d4-b77f-8e3a546f2f31
pszAttributeName : dNSHostName
ObjectClass : server
DN : CN=PC1\0ADEL:de838231-3f87-47d4-b77f-8e3a546f2f31,CN=Servers,CN=Default-First-Site
-Name,CN=Sites,CN=Configuration,DC=example,DC=local
ObjectCategory :
SamAccountName :
dwVersion : 1
WhenCreated : 2019-02-23 02:12:15Z
Member :
ftimeCreated :
ftimeDeleted :
SID :
pszLastOriginatingDsaDN : CN=NTDS Settings,CN=DC2,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configur
ation,DC=example,DC=local
uuidLastOriginatingDsaInvocationID : 97c9ab0f-143e-4218-96fb-a6bdc442af7e
usnOriginatingChange : 24859
usnLocalChange : 45319
<add>
I got a comment in DM. The following time stamps show the same value. Promotion and deletion of DC occurred at the same time.
ftimeLastOriginatingChange = WhenCreated
</add>
The "log-adexport.log" file contains the output related to DCshadow.I have failed to run DCshadow once, so it is recorded twice. ;-)
2019-02-23 02:31:30 Domain Controller demotion or use of DCShadow: 2 deleted server objects and 2 deleted nTDSDSA objects located in the tombstone
You can also check records related to Bob's SIDHistory with ADTimeline.
ftimeLastOriginatingChange : 2019-02-23T02:12:15Z
Name : bob
pszAttributeName : sIDHistory
ObjectClass : user
DN : CN=bob,CN=Users,DC=example,DC=local
ObjectCategory : CN=Person,CN=Schema,CN=Configuration,DC=example,DC=local
SamAccountName : bob
dwVersion : 1
WhenCreated : 2019-02-11 07:06:37Z
Member :
ftimeCreated :
ftimeDeleted :
SID : S-1-5-21-1490397982-2793378994-64436834-1601
pszLastOriginatingDsaDN :
uuidLastOriginatingDsaInvocationID : d5bc3667-ea75-4e13-a074-70f751b5e55c
usnOriginatingChange : 24822
usnLocalChange : 45335
The number of SIDHistory is output in the "log-adexport.log" file.
2019-02-23 02:31:30 Number of accounts with SIDHistory in the forest: 1
2019-02-23 02:31:30 Number of accounts with a suspicious SIDHistory in the current domain: 1
Let's check the properties of Bob account.
The SID of Administrator is set in SIDHistory of Bob account. On DC 2, the time stamp of whenChanged is "2/23/2019 2:12:15 AM".
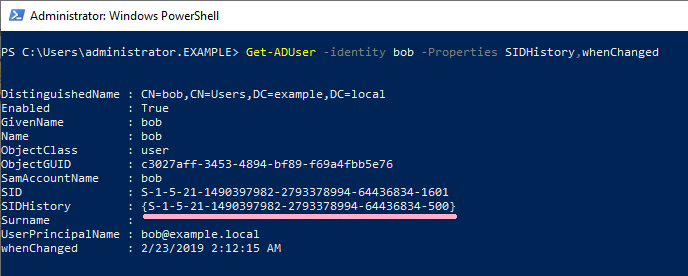
On DC1, the time stamp of whenChanged is "2/23/2019 2:12:30 AM".(Whenchanged is not replicated.)
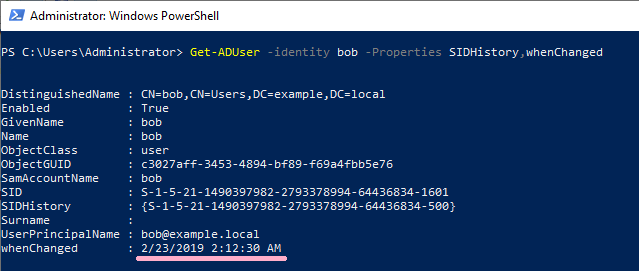
What is the change at 2:12:30? , I confirmed the event log but could not identify it.
You can download timeline and event log from here.
I will continue testing.
Verification environment: Windows Server 2019 1809, Windows 10 1809, Time zone UTC
Reference URL:
When-Changed attribute - Windows applications | Microsoft Docs
