Note:I translated Japanese into English using Google Translate.
Thank you, Google.
Today, I would like to confirm the NTFS symbolic link.
Copy the JPEG file to the sample VHD Disk.
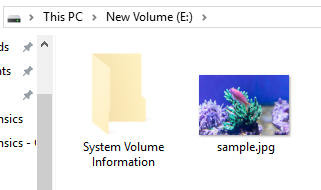
Use the mklink command for this JPEG file to create a symbolic link.
The link name is exempl.jpg.
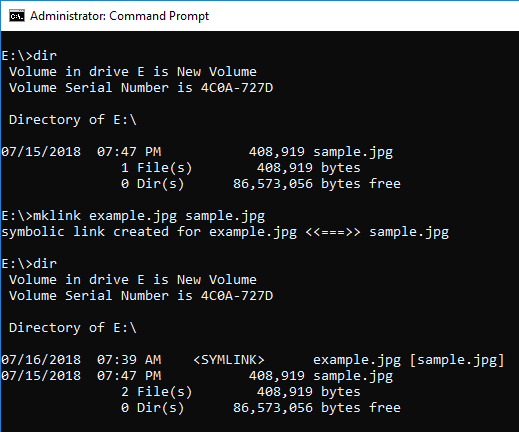
When browsed from the explorer, it can be identified by the icon image.
Use Autopsy to browse this volume. It seems difficult to identify a symbolic link from the file list.
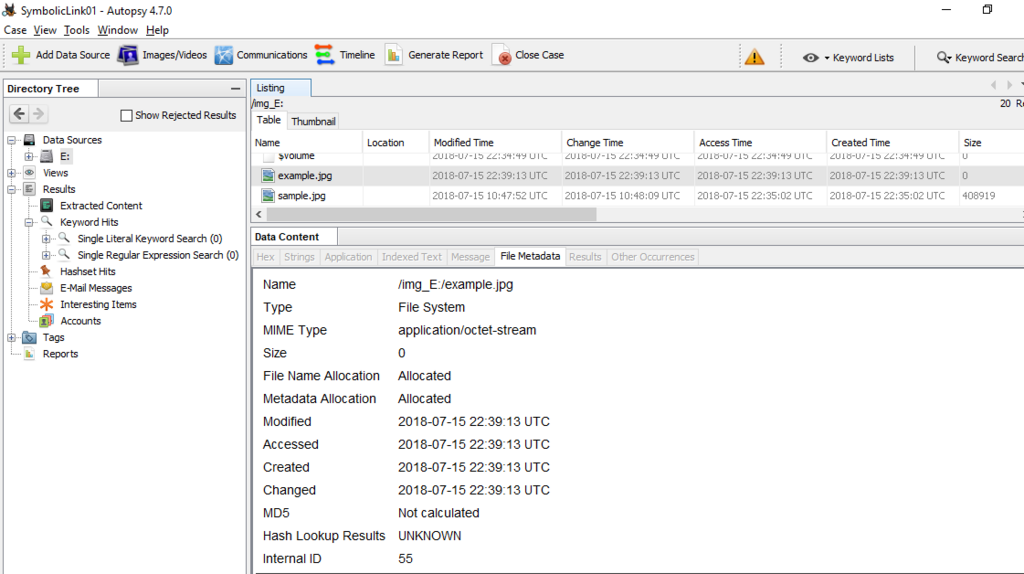
You can find $REPARSE_POINT in the Attributes field.

Let's look at $REPARSE_POINT (0xC0) in the FILE record.
Display offset 44032 in $ MFT. The range enclosed in red color starting from 0xC0 is $REPARSE_POINT.
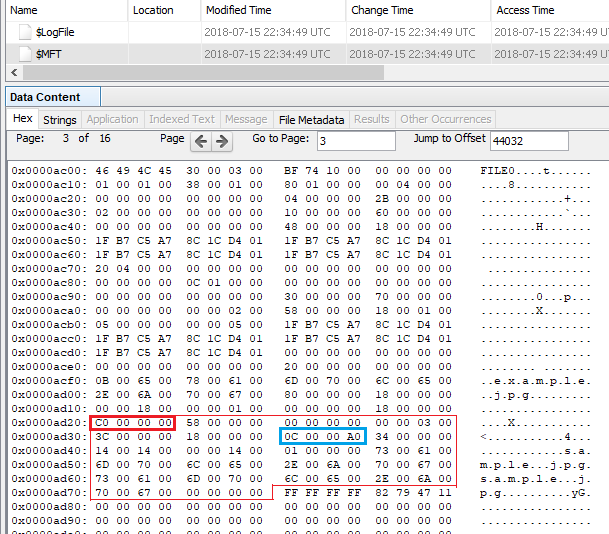
The range of 0C0000A0 enclosed in light blue is Reparse point tag. 0xa000000c means Symbolic link.
0C 00 00 A0 Reparse point tag ⇒ Symbolic link
34 00 Reparse data size ⇒ 52
00 00 Reserved
14 00 Substitute name offset ⇒ 20
14 00 Substitute name size ⇒ 20
00 00 Print name offset
14 00 Print name size ⇒ 20
01 00 00 00 Symbolic link flags
730061006D0070006C0065002E006A0070006700 sample.jpg
730061006D0070006C0065002E006A0070006700 sample.jpg
00000000
Using MFTECmd is simpler than visual inspection.
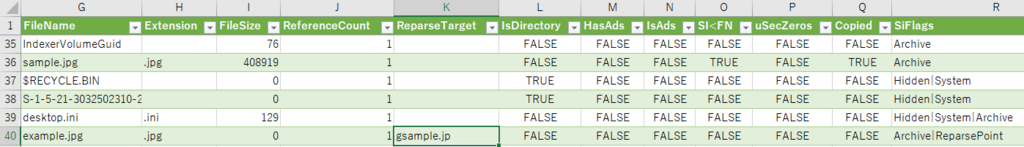
I do not know what "g" means....Interesting....The character at the end of the file is at the beginning.
<2018/07/17 add >
so i found and fixed a goofy fringe issue based on this post. Grab MFTECmd 0.2.8.0 and see how it looks now. For some reason, the print name offset was 0. i was off by 2 in this case as well, but it should be good now. More test data FTW! pic.twitter.com/wGMmFRNsy2
— Eric Zimmerman (@EricRZimmerman) July 16, 2018
</add>
Delete sample.jpg and overwrite the FILE record.
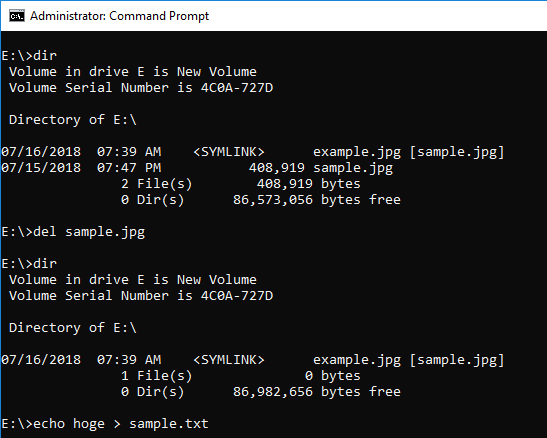
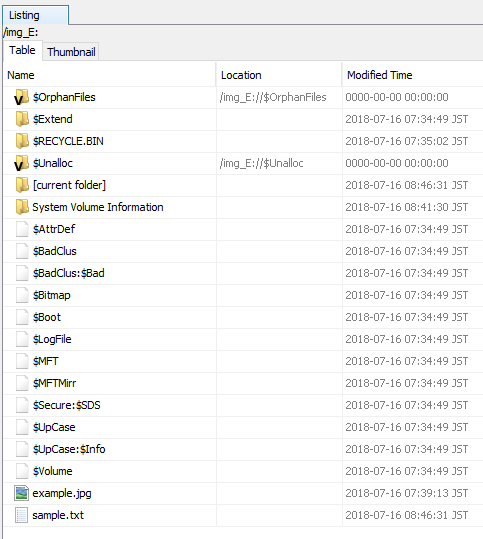
By creating sample.txt, sample.jpg can not be confirmed.
If you use MFTECmd, you can find example.jpg with the value of ReparseTarget.
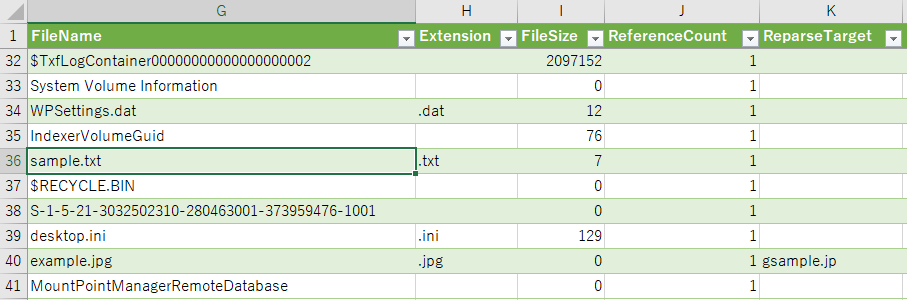
When you find a symbolic link, let's check the reference.
Reference URL:
