Windows ID 4648 "A logon was attempted using explicit credentials"
Note:I translated Japanese into English using Google Translate.
Thank you, Google.
Summary:
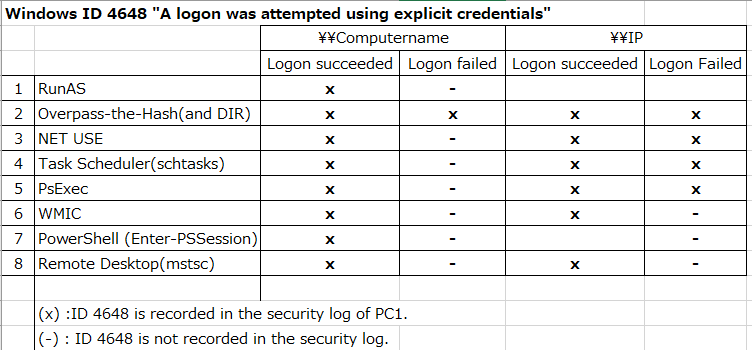
- Check when the ID 4648 occurs.
- Runas,Overpass-the-Hash,NET USE,Task Scheduler(schtasks),PsExec,WMIC,PowerShell,Remote Desktop(mstsc)
- If authentication fails, it differs depending on whether you specify a computer name or IP address.
- If you specify an IP address instead of a computer name, the contents of "Additional Information" will differ.
----------
What kind of user operation is event ID 4648 recorded?
The conditions for recording event ID 4648 are described by Microsoft at the following URL.
4648(S) A logon was attempted using explicit credentials. (Windows 10) | Microsoft Docs
Event Description:
This event is generated when a process attempts an account logon by explicitly specifying that account’s credentials.
This most commonly occurs in batch-type configurations such as scheduled tasks, or when using the “RUNAS” command.
I would like to try some of the operations described above.
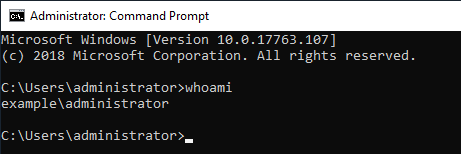
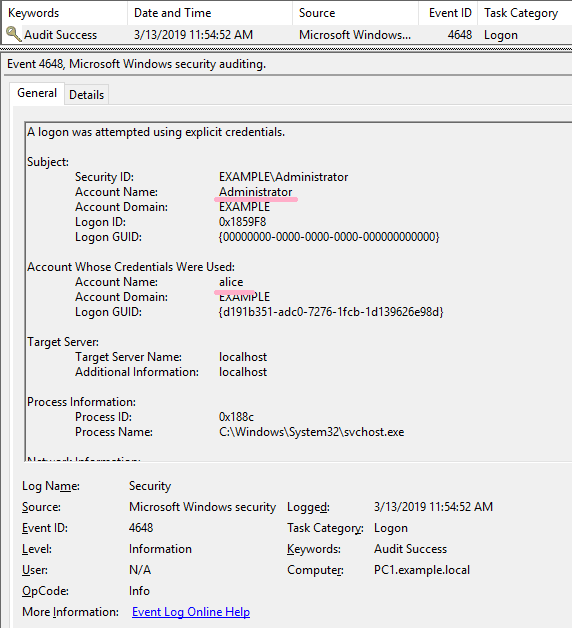
logged on to PC1 with Example\administrator. Confirm the ID 4648 by switching from the administrator account to the Alice account.
(1)Runas
First, change the account to Alice with the Runas command. (Alice account is a user of domain. Also, Alice account is included in Domain Admins.)
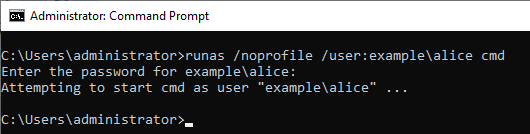
Entered Alice's password and RunAs succeeded.
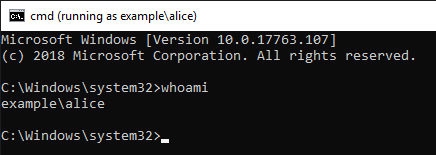
ID 4648 is recorded in the security log.
What happens if the authentication fails?
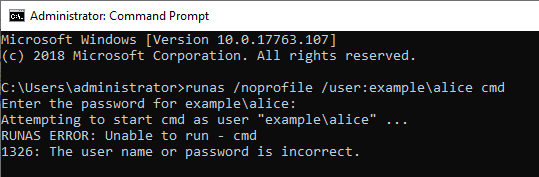
If the Runas command was not successful, I could not find ID 4648 in the security log.
(2)Overpass-the-Hash
Execute Overpass-the-Hash using Alice's NTLM hash value. ID 4648 has not occurred in this operation.
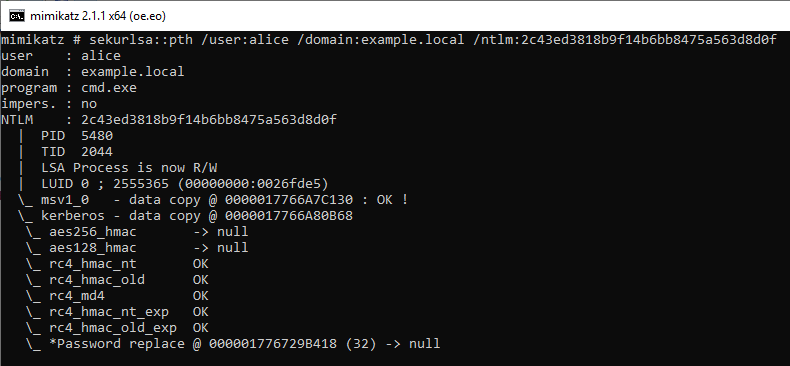
Execute the DIR command on the PtH CMD. By this operation, ID 4648 is recorded in the security log of PC1.
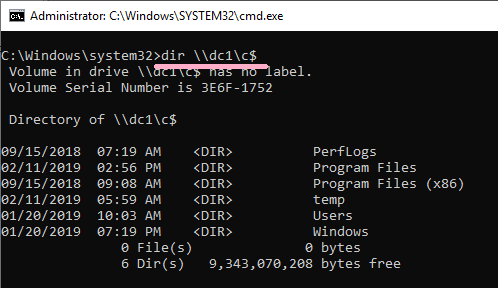
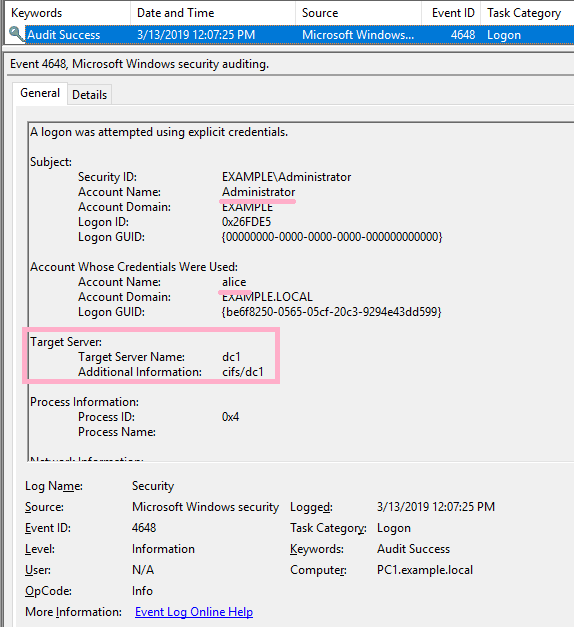
Connect to DC1 using the wrong hash value.
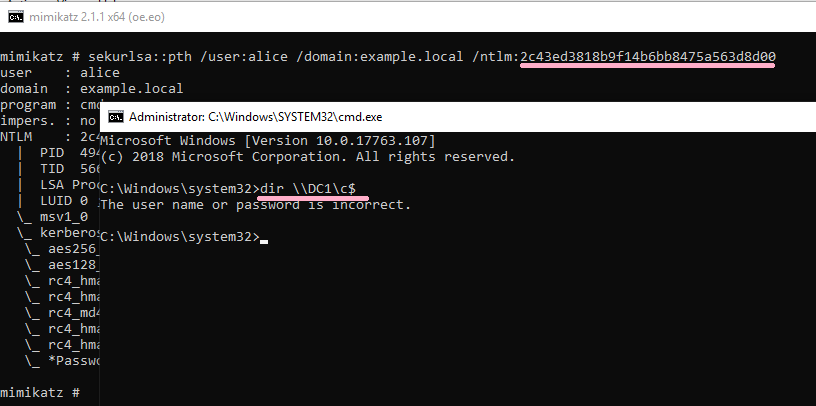
DIR command failed, but the ID 4648 was recorded.
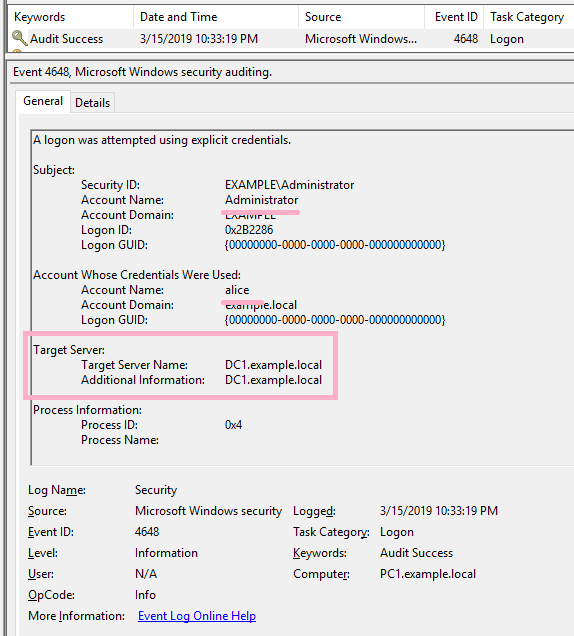
(3)NET USE
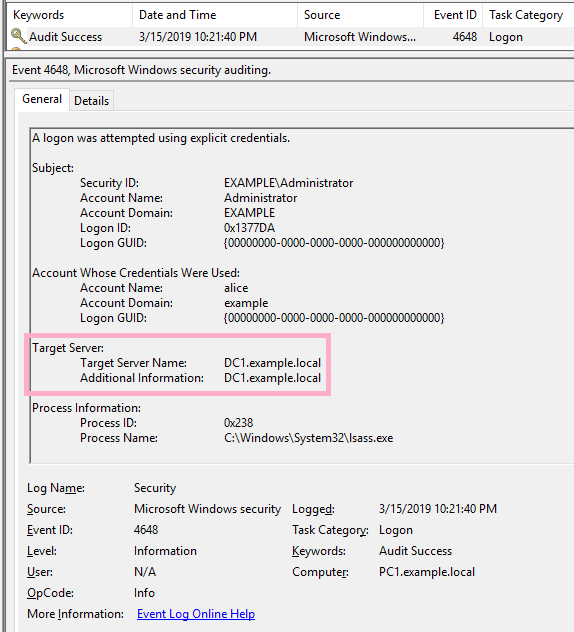
I started Administrator's CMD newly and executed the NET USE command. Specify Alice account with /user option. (The command line specifies the computer name. Kerberos authentication is used.)
ID 4648 is recorded in the security log of PC1.
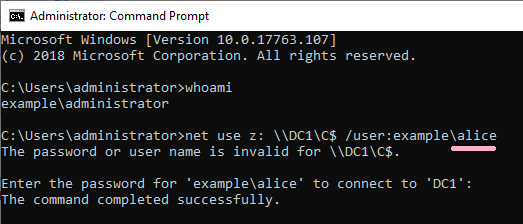
If the command was not successful, I could not find ID 4648 in the security log.
However, if you specify an IP address other than computer name, ID 4648 will be recorded.
(4)Task Scheduler(schtasks)
Use the schtasks command to register a job on the remote system.
(I got an error a little ;-)
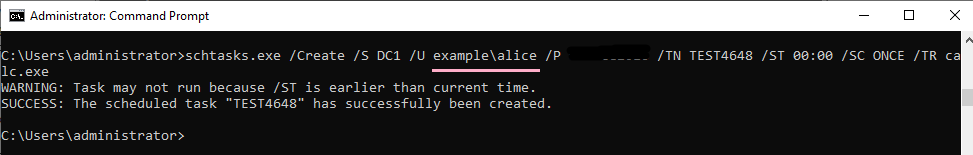
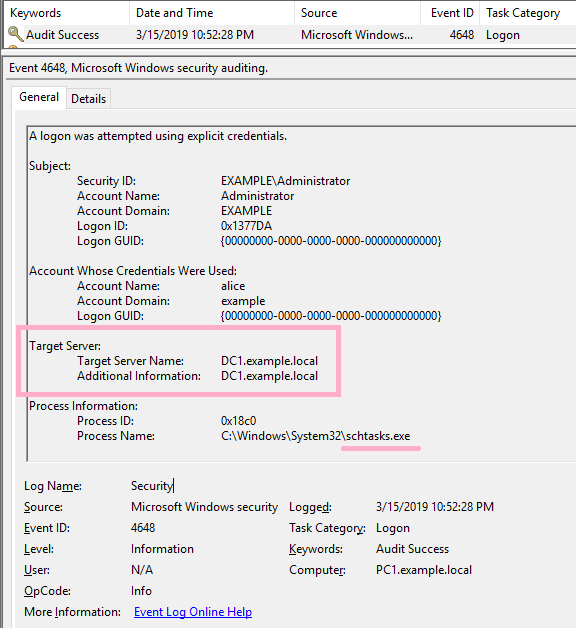
ID 4648 is recorded in the security log of PC1. The contents of "Additional Information" is "host/DC1".
If the command was not successful, I could not find ID 4648 in the security log.
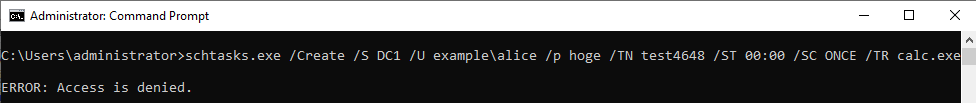
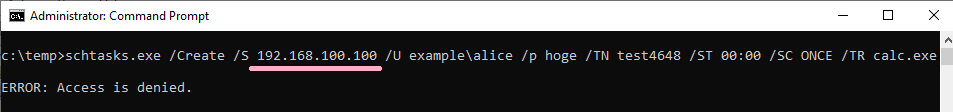
If you specify an IP address and authentication fails, ID 4648 will be recorded.
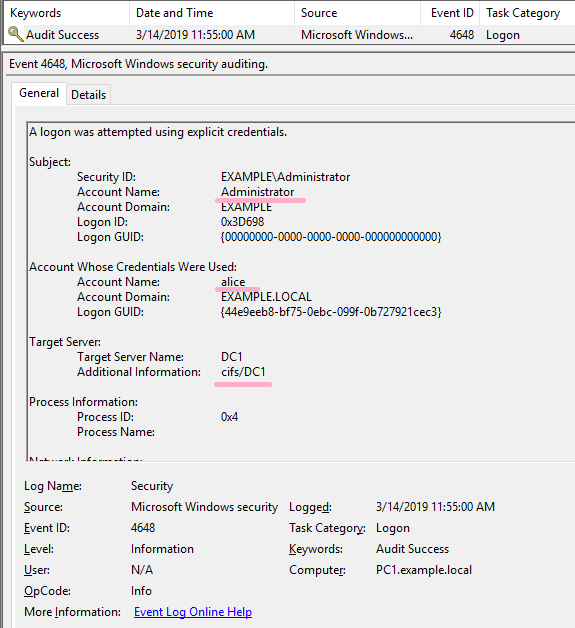
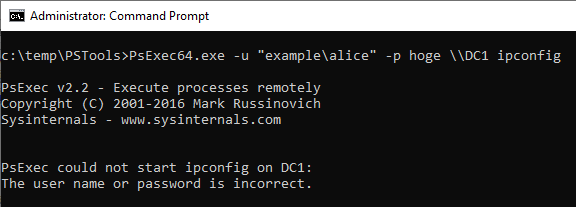
(5)PsExec
Execute ipconfig command on DC1 using PsExec command. Specify Alice account with -u option.
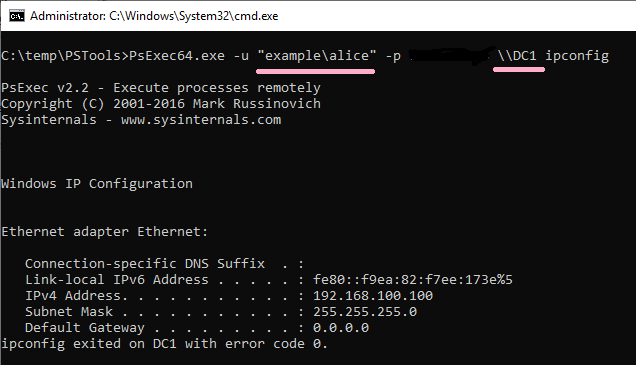
ID 4648 is recorded in the security log of PC1. The contents of "Additional Information" is "cifs/DC1".
If the command was not successful, I could not find ID 4648 in the security log.
If you specify an IP address and authentication fails, ID 4648 will be recorded.
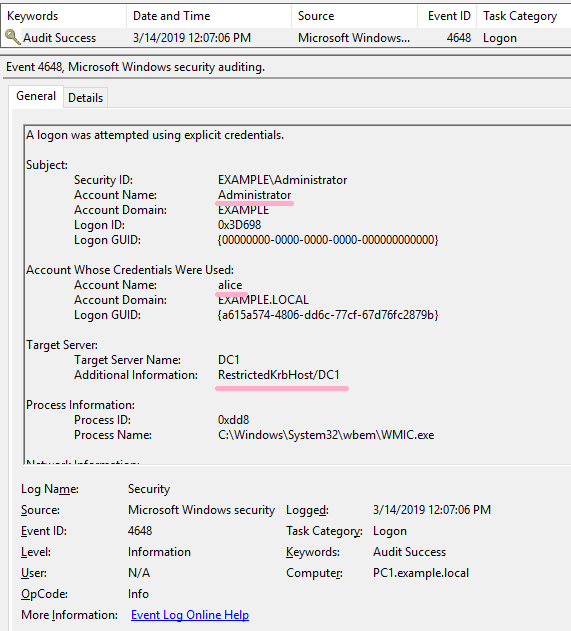
(6)WMIC
Execute ipconfig command on DC1 using WMIC command. Specify Alice account with /user option.
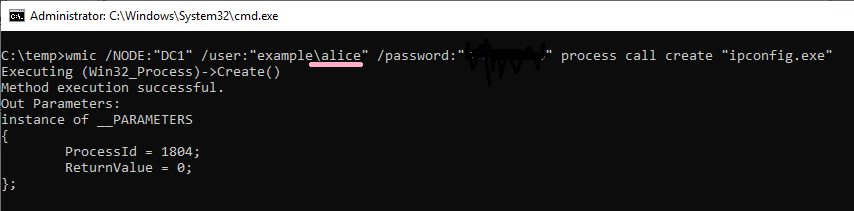
ID 4648 is recorded in the security log of PC1. The contents of "Additional Information" is "RestrictedKrbHost/DC1".
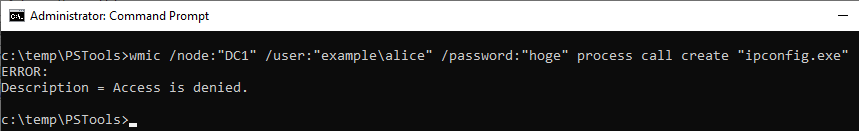
If the command was not successful, I could not find ID 4648 in the security log.
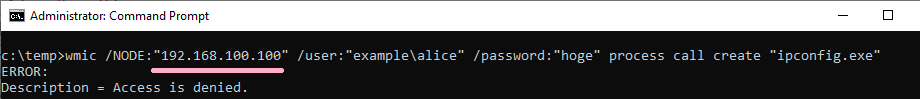
If you specify an IP address and authentication fails, ID 4648 was not recorded.
(7)PowerShell
Execute Powershell and Enter-PSSession. Specify Alice account with -Credential option.
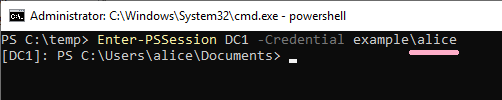
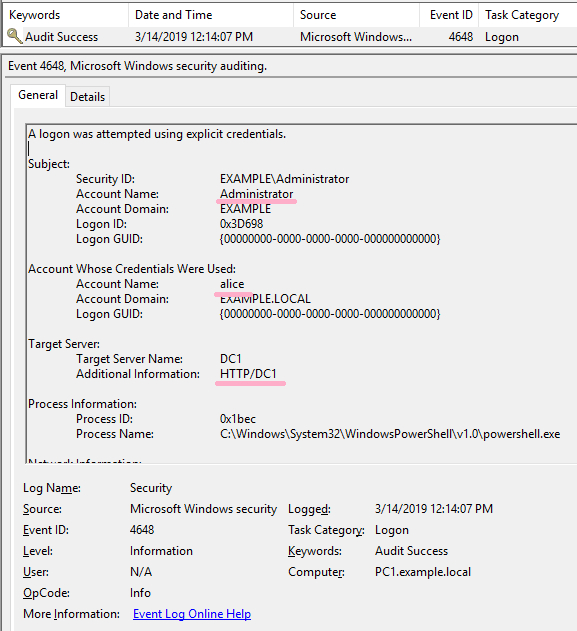
ID 4648 is recorded in the security log of PC1. The contents of "Additional Information" is "HTTP/DC1".
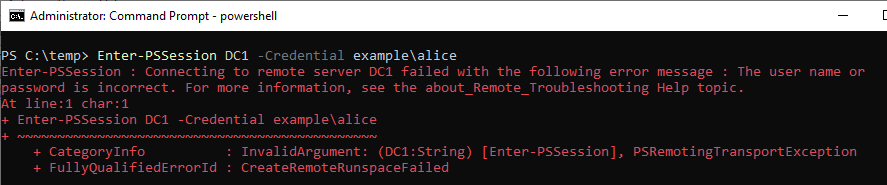
If the command was not successful, I could not find ID 4648 in the security log.
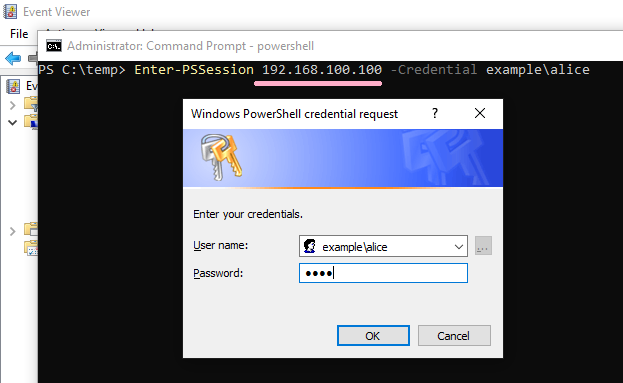
If you specify an IP address and authentication fails, ID 4648 was not recorded.
(8)Remote Desktop(mstsc)
Execute mstsc command. Specify Alice account.
(NLA is enabled on DC1.)
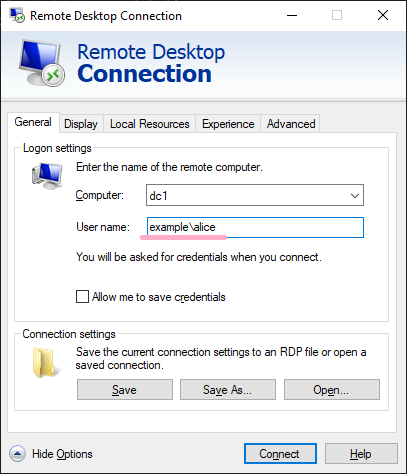
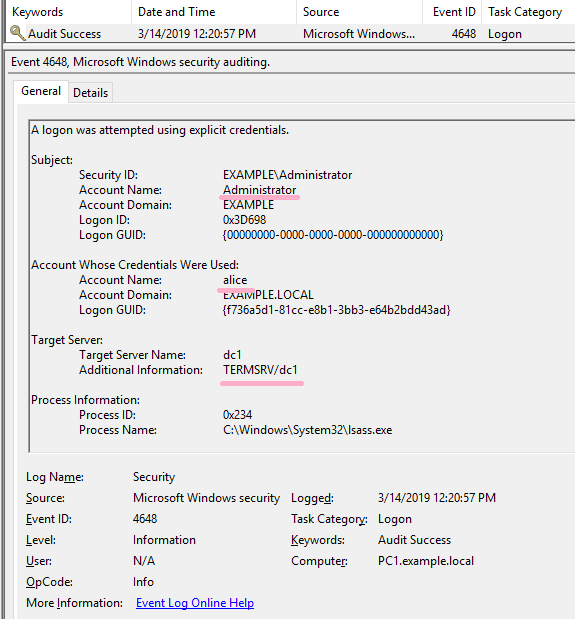
ID 4648 is recorded in the security log of PC1. The contents of "Additional Information" is "TERMSRV/dc1".
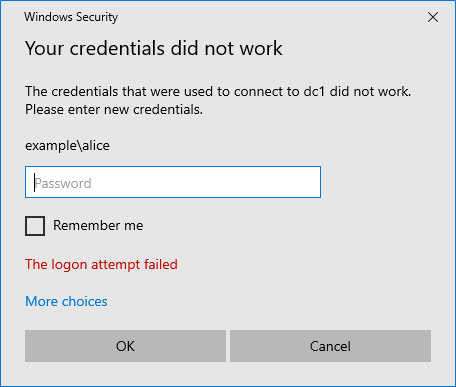
If the connection was not successful, I could not find ID 4648 in the security log.
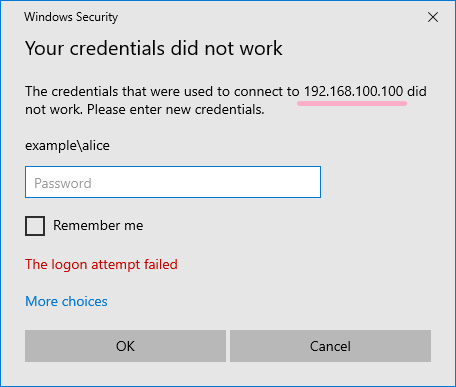
If you specified an IP address as the computer name, ID 4648 was recorded in the security log even if authentication failed.
The details of RDP and ID 4648 are described in "Event Log Analysis" of IIJ-SECT.
It also explains the case where ID 4648 is not recorded when using "Restricted Admin mode". Please refer to the following URL.
https://sect.iij.ad.jp/d/2018/05/044132/training_material_sample_for_eventlog_analysis.pdf
Verification environment: Windows Server 2019 1809, Windows 10 1809, Time zone UTC
Reference URL:
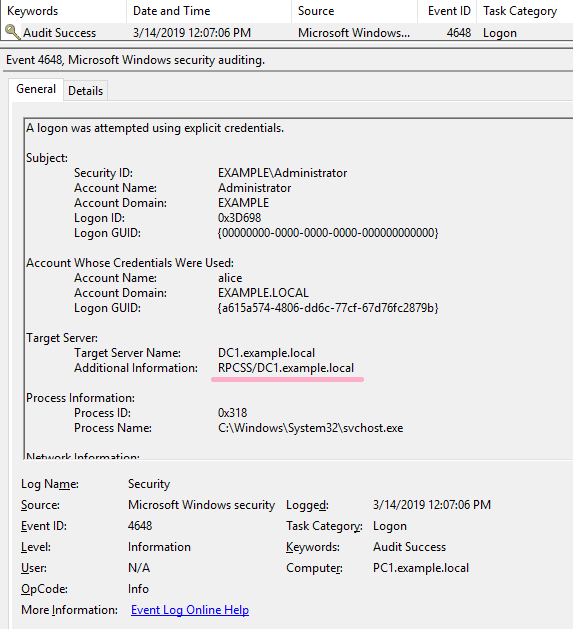
[Lateral Movement - RPC over TCP/IP] - can be hunted using only 4648 (usually available) with Additional Information pointing to RPCSS SPN. #ThreatHunting #DFIR pic.twitter.com/7xsOcildbz
— MENASecurity (@menasec1) March 18, 2019
https://sect.iij.ad.jp/d/2018/05/044132/training_material_sample_for_eventlog_analysis.pdf
